Project Summary
The project
This effort focused on redesigning the Vulnerability Remediation experience within the ConnectWise Asio security platform. Although positioned as “Vulnerability Management,” the existing experience was architected around managing vulnerability scans, requiring users to navigate system structure before they could take action.
The redesign shifted the experience from scan-centric navigation to a vulnerability-first workflow, enabling users to understand risk and remediate issues without drilling through multiple layers of hierarchy.
Core user problem
Users needed a fast, clear way to remediate vulnerabilities across devices, but the platform forced them to work backwards through scan data, organizational structures, and device hierarchies. Remediation actions were buried behind scan details, increasing cognitive load and turning a time-sensitive security task into a navigation problem.
My role, scope, and collaborators
I led UX design for the remediation experience, owning information architecture, task flows, responsive layouts, and remediation workflows. I produced user flows, interactive Figma prototypes, and usability tests, and worked closely with a product manager and an embedded scrum team.
Throughout the project, I partnered with engineering to validate designs against the design system, API availability, and MVP constraints, ensuring the solution was both usable and buildable.
Constraints and challenges that shaped the work
Quantitative Data
Several years of behavioral data from Pendo showed low engagement with scan-level pages and significant drop-off during remediation flows. Users rarely explored scan details unless forced, confirming that scans were not a meaningful decision surface for remediation tasks.
Qualitative insights
I gathered continuous feedback from early access users who consistently expressed frustration with deep navigation, lack of visibility into impacted devices, and uncertainty about where to begin remediation. Stakeholders echoed these concerns, emphasizing the need for clearer prioritization and faster paths to action.
Design Approach
Designing around the vulnerability, not the scan
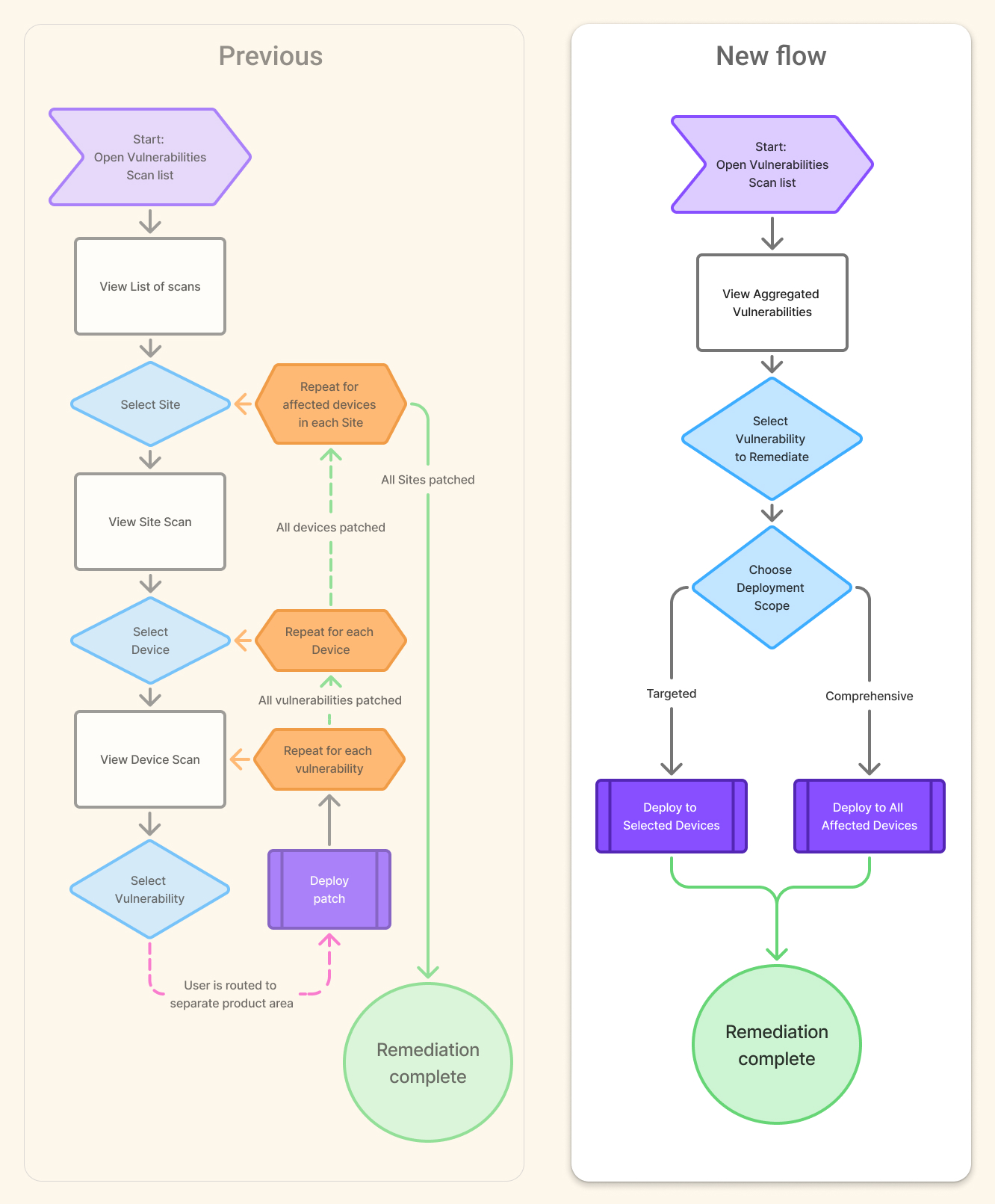
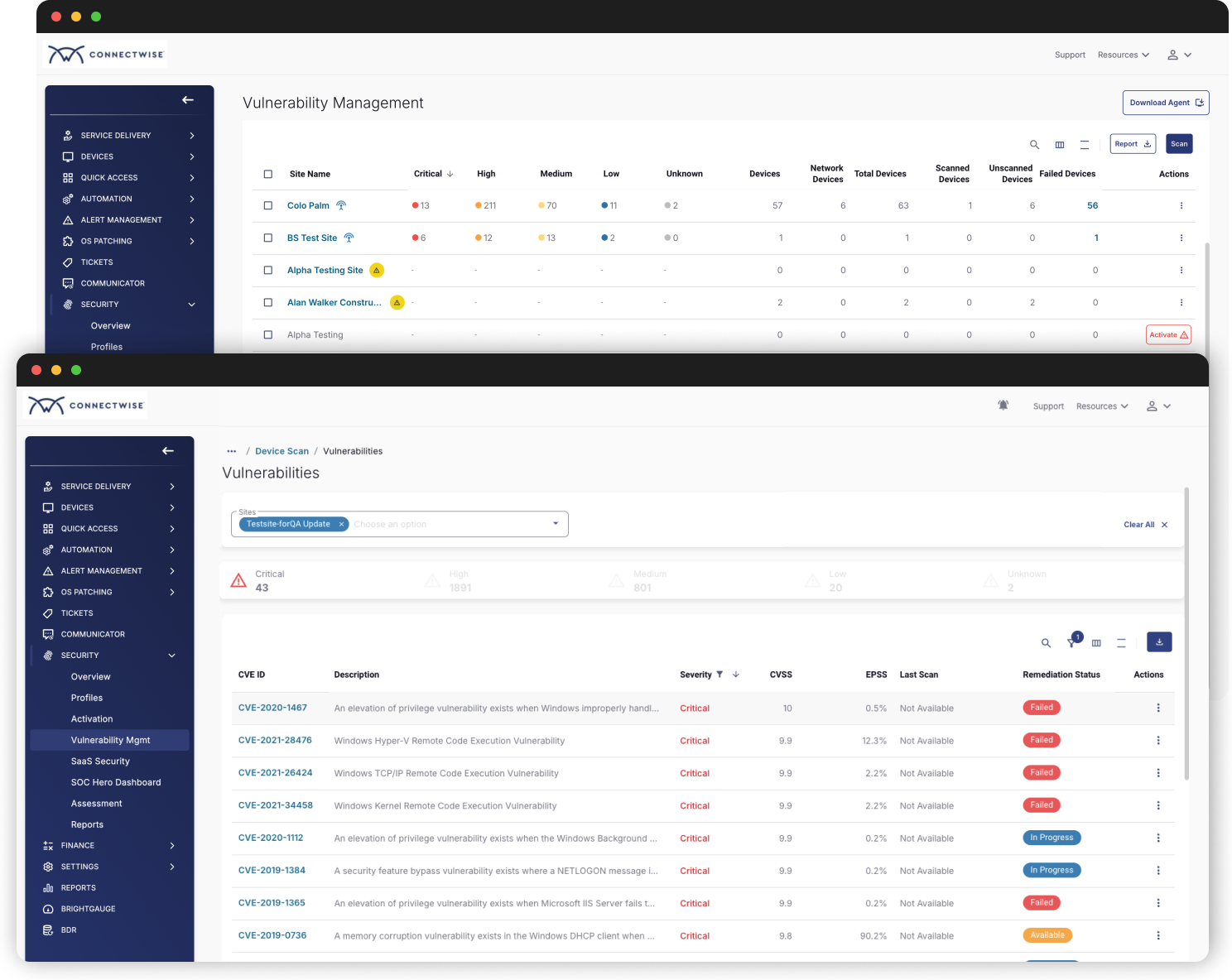
The core design decision was to make vulnerabilities the primary unit of work. The redesigned dashboard aggregates detected vulnerabilities up front, allowing users to assess risk immediately rather than navigating through scans, companies, sites, and devices.

Reducing navigation and decision fatigue
Remediation workflows were streamlined into a single decision point: deploy a fix to selected devices or all affected devices. This collapsed multiple repetitive flows into one clear action, reducing context switching and cognitive load.
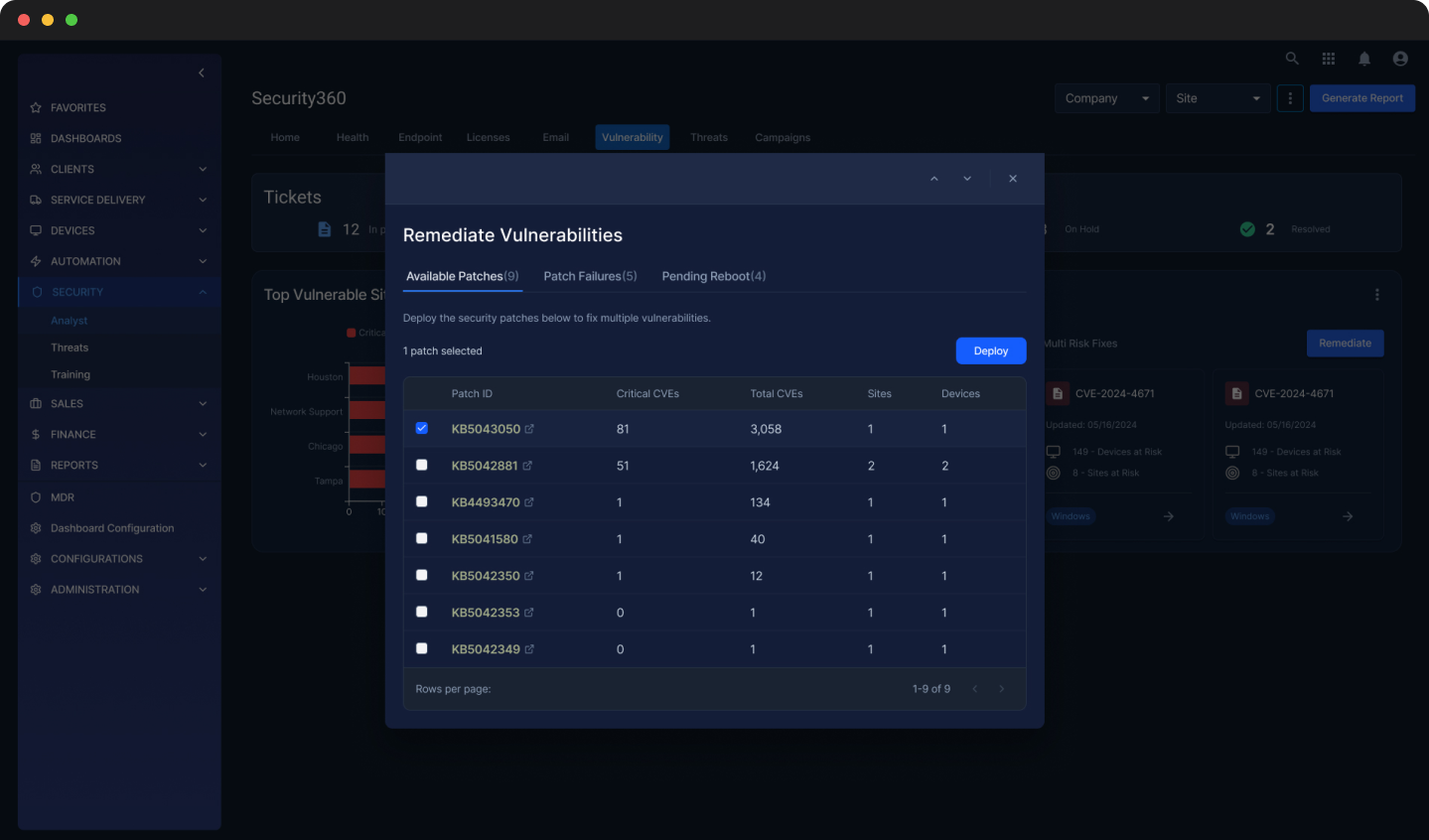
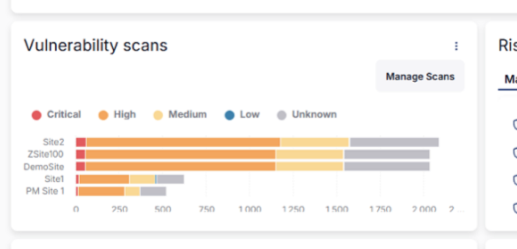
Placing scans in the background
The vulnerability scans were folded into the setup process. Users could still view individual scans and set the cadence. Once scans were set up though, we observed that the schedule controls were rarely accessed.
Balancing consistency with platform constraints
Because patch deployment existed elsewhere in the platform, the remediation flow was designed to feel familiar without being identical. Component usage, language, and interaction patterns aligned with the broader system while accommodating API and MVP limitations.
Outcome/Reflection
Lessons learned
The redesigned vulnerability remediation experience became the primary way users move from detection to action within the platform. By shifting the workflow to a vulnerability-first model, the experience reduced navigation depth, clarified decision-making, and aligned remediation with real-world security tasks.
The work established a clearer, more scalable foundation for vulnerability management and helped position remediation as a core capability.